ipv6 home router experiments
KubeCon this year featured a panel discussion of IPv6 adoption. One of the panelists mentioned in passing that many organizations are unprepared for the security implications IPv6. With IPv4, most addresses were hidden by NAT; with IPv6, addresses are publicly routable. Firewalls can block external traffic, but might not be configured correctly.
So I did an experiment on my home network. Would enabling IPv6 expose my devices on the public internet?
I found an “IPv6” panel in my router configuration. First, I changed the “Internet Connection Type” drop-down menu to “Auto Detect”, then the Netgear router switched to “Pass Through”. I guess my ISP supports IPv6?
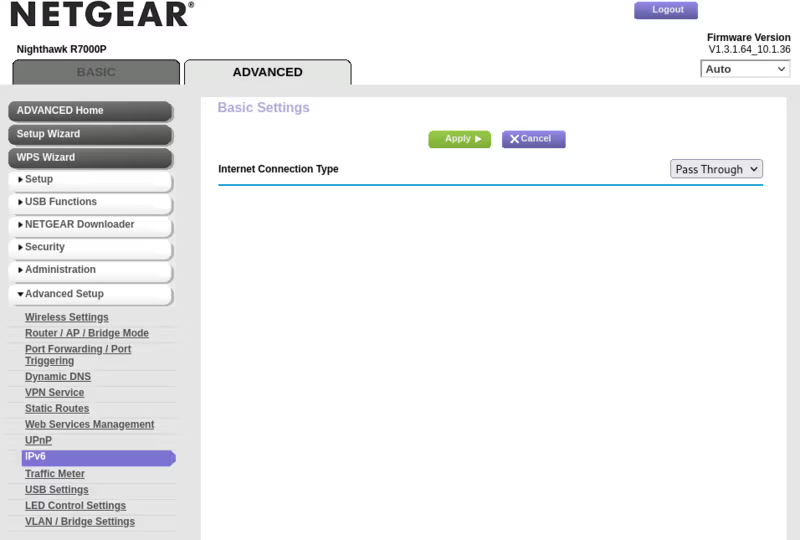
Yes! My devices were assigned IPv6 addresses!
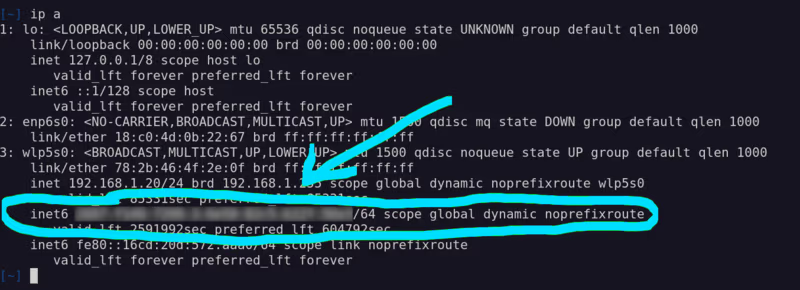
From a computer outside my network, I tried to ping the IPv6 address:
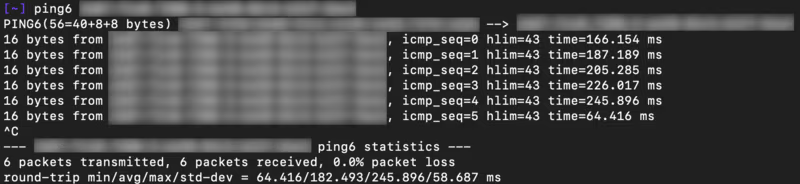
Success! The address is reachable and responding to ICMPv6 pings.
Next, I tried an HTTP request to a server listening on port 1313.

Yep, that worked too!
It seems that my Netgear router does not provide an IPv6 firewall. (It does, however, block external IPv4 traffic; I got no response from ping or curl to the router’s public IPv4 address.)
Here’s a difference, though. With IPv4, when I exposed ssh port 22 to the public internet, I’d see hundreds of failed login attempts per day. This hasn’t happened with IPv6 – in the last month, I’ve seen zero attacks. Why?
I looked up the prefix of the IPv6 address and found the organization that’s providing my internet service. They’ve reserved a /32 subnet (296 possible addresses). By capturing ICMPv6 packets with tcpdump -v -i en0 icmp6, we can see the router advertising a /64 prefix:
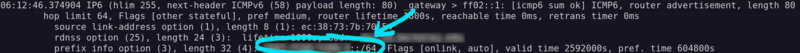
My ISP is assigning addresses from a subnet 232 times larger than the entire IPv4 internet. I’m not sure if they are using different prefixes for other apartments (they certainly have enough to do so!), but even so, that’s a lot of address space for not-very-many devices.
The IPv6 address space is so massive that it’s impractical to find a target by scanning. That’s helpful, but not enough – we still need firewalls in IPv6. Obscurity ≠ security and all that.